Checkmarx - V 1
What is Checkmarx?
Checkmarx enables you to run a series of scanners on each of your projects, each identifying risks affecting different aspects of your software development and deployment.
Checkmarx's core functionalities, such as integration with CI/CD and IDEs, Policy configuration, Triaging results etc. are available across scanners. The platform is designed for the cloud development generation and is delivered from the cloud. It seamlessly secures your entire codebase, enabling you to deliver and deploy more secure code.
Service-Now Ticket Integration
Weekly scans are performed against all running Stage and Production instances. The scan results are recorded in Checkmarx using the format {appcode}/{repo_name}/{namespace}/runtime. The Critical+High vulnerabilities found from the scans generate AVIT's (Application Vulnerability Item Ticket) in Service-Now. These tickets are assigned to the assignment group listed in CMDB for the respective application.
Pipeline Integration
Scans will be performed each time a pipeline is run. The scan results are recorded in Checkmarx using the format {appcode}/{repo_name}/pipeline. A link to the scan results will be available in the 'Checkmarx' stage within the 'Security' job of the pipeline. This 'Checkmarx' stage will also show you the vulnerabilities found, along with the SLO before the pipeline is blocked. If the SLO is not met, the pipeline will still run, however the production deployment stage of the pipeline will be blocked. Checkmarx blocking is not enabled. It will be enabled at a future date (TBD).
| Severity | Ticket Remediation SLO | Pipeline Blocking SLO |
|---|---|---|
| CRITICAL - ZERO DAY | Immediate | TBD |
| CRITICAL | 15 Days | TBD |
| HIGH | 30 Days | TBD |
| MEDIUM | 90 Days | N/A |
| LOW | 180 Days | N/A |
Custom Repos and Scans
The pipeline integration is enabled for pipeline versions v4.5 and above. Repositories that use our SCALE pipeline will automatically create an associated project in Checkmarx. If you would like to scan a repo that is not managed by our SCALE pipeline, please specify the project name in the format of {appcode}/{repo_name}/manual (see the 'Applications and Projects' section below).
Login
- Navigate to: https://us.ast.checkmarx.net/
- If prompted for the tenant, use 'netapp'
- At the login page, there is no need to fill out the username & password fields. Instead, click the "NetApp SSO" button at the bottom of the login form.
Applications and Projects
Checkmarx uses the terms "Applications" and "Projects". Each application will have its own "Application" in Checkmarx, listed as the 3-letter appcode of the application. Each repository will have its own "Project" in Checkmarx. The Project name will be in the format {appcode}/{repo_name}/*. Within each project, you will see results for multiple scan types (SCA, SAST, Container, etc..).
Viewing scan results
IDE Integration
False-Positives
If a finding is a false positive, members of ng-ngdc-{appcode}-dev have the ability to update the finding as "Propose Not Exploitable". A note in the form might be required before saving the change. A member of ng-ngdc-{appcode}-leads have the ability to mark findings as "Not Exploitable". Once a vulnerability of a '*/pipeline' project is marked Not Exploitable, the pipeline will ignore it. Once a vulnerability of a '*/runtime' project is marked Not Exploitable, the Service-Now ticket will close the following day and ignore it.
Note: To mark a 'false positive', please set the state to 'Not Exploitable'.
- Triaging SAST Results
- Triaging SCA Results
- Triaging IaC Security Results
- Triaging Container Security Results
Pipeline Blocking Exception Process
If you are unable to remediate the vulnerability within the SLO, your pipeline will block future production deployments. If you need to file a temporary exception, please follow the process outlined in the following flowchart:
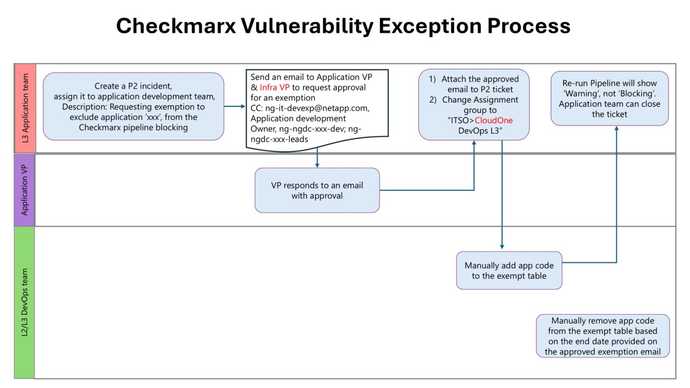
Training Video
The following Checkmarx training video provides a detailed exploration of key topics, including an overview of Checkmarx, integration with pipelines, authentication processes, vulnerability assessment techniques, and pipeline blocking mechanisms. Join us to enhance your understanding of Checkmarx and fortify your application security practices.
FAQ's
Contact
If you run into any issues or have questions, please open an INC ticket assigned to ITSO > CloudOne DevOps L3